Security
]project-open[ has been designed from scratch to operate in a hostile Internet environment and across competing organizations. Security has received intensive attention ever since.Role-based security model
Effective collaboration on projects and other tasks require access control of critical knowledge assets. Not every employee of a company should be able to access conversations on other projects, access the list of customers or see financial reports.
In order to allow for collaboration, ]project-open<[ implements a fine-grained, role-based permission scheme, allowing to configure access permissions to all important information assets based on roles or profiles of users. This way, every project becomes an e-room and external project team members will only be able to access the information they need to see.
TCL script language
The underlying OpenACS online-community platform runs on TCL, an interpreted scripting language. Being an interpreted language, TCL eliminates the thread of buffer overflows, the #1 reason for security vulnerabilities. Being an non-standard and "exotic" language in the realm of Web applications, a potential attacker would have to learn the specifics of the language and its libraries in order to search for vulnerabilities.
Highly secure AOLserver Web server
"AOLserver is the backbone of the largest and
busiest production environments in the world"
(www.aolserver.com)
]project-open[ web services are provided by AOLServer, a leading Web and application server for large online communities. AOLServer has received intensive attention and investment from AOL because it is the base of its infrastructure. Thanks to open-sourcing AOLserver, the code has then gone through the scrutinity of the open-source development process ("given enough eyballs, all bugs are shallow").
The combination of professional software management (by AOL), high visibility and high "obscurity" results in a security level magnitudes above the one of other popular Web servers and makes it unattractive for authors of viruses, worms and exploits. There was only a single vulnerability of AOLServer in the last seven years, while there were hundreds of such incidents for the Microsoft IIS and Apache web servers.
Automated system updates
]project-open[ by default runs on CentOS/Red Hat Enterprise Linux. This linux flavour is known for its sturdyness and receives daily security fixes via its YUM update mechanism. The ]project-open[ application itself is equipped with the ASUS Automatic Software Update Service, providing rapit patches for critical vulnerability.
Application Security Features
The OpenACS platform underlying ]project-open[ is equipped with a number of outstanding security features not found in common Web architectures such as Java, PHP or .NET. "Page contracts" filter parameters coming through URLs or FORMS for data type and invalid HTML characters and cross-site scripting, "colon variables" (see below) eliminate the risk of SQL injection and an integrated "alert system" will inform administrators about any attempt of tinkering with the system.
Background: What is security?
The goal of computer security is to avoid
- the loss,
- false creation,
- alteration or
- unauthorized distribution
of the data stored in a computer system.
The loss of data can be avoided by regular data backups. The other three elements (false creation, alteration or unauthorized distribution) are related to Internet Security.
Internet security is like a chain...
Security is like a chain that breaks at its weakest point. The pieces of the chain consist of:
- The users environment (his computer, where the user stores his passwords, ...)
- The Internet transmission (the users service provider, ...)
- The server operating system (Linux, Windows, ...)
- The web server (AOLServer)
- The software application (OpenACS and ]project-open[)
- The security configuration of the ]project-open[ application.
Below we are going to explain you how we take car for each of these pieces of the chain. But first it is important to understand the nature of security threads.
Who is attacking?
The vast majority of security-related damage is caused by unhappy or ex- employees. This may sound surprising, but your sales data for example are not very attractive to a regular Internet hacker.
The second largest source of damages is due to errors of system administrators (and not related to Internet security at all).
Internet security only ranks third and fourth in the list of threads, due to worms and trojans at the third place and Internet hackers at the fourth.
Assessing security risk
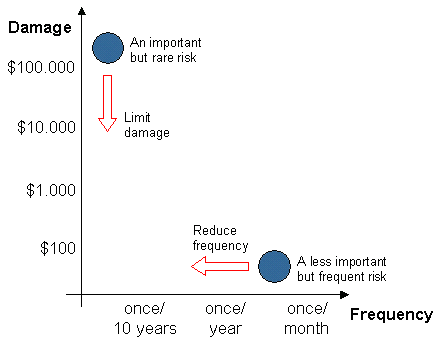
|
|
|
Security risks:The cost is damage x frequency |
|
What is the damage to you if your sales data get into the hands of your competitors? Where are the most likely sources? How would you try to steal the sales information of your competitors?
Technical Details
This section is designed to provide IT security experts with details on the sections above to allow them to verify the security relevant claims .
Page Contracts
A "page contract" is a formal description of the input variables of an application page, similar to a procedure declaration in a procedural programming language. Its purpose is to extract and filter URL and FORM parameters coming from the hostile Internet envionment and to map them into local variables.
A page contract consists of a documentation section (comments on the purpose of the page), and a parameter section defining the expected parameters. The page contract will identify and report values that don't match with the declarations.
In the example below, the parameter "absence_id" needs to be an integer. It defaults to "0" if no value is explicitely specified. "Description" is explicitely allowed to contain certain HTML tags (configurable), while HTML tags are prohibited for all other variables by default.
ad_page_contract {
Save the changes after modifying an existing absence.
@param absence_id The unique ID of the absence
@param owner_id Absence initiator
@param start_date Absence start
@param end_date Absence end
@param description Description of the absence item
@param return_url Where to return?
} {
{absence_id:integer 0}
owner_id:integer,notnull
start_date:date,notnull
end_date:date,notnull
description:trim,html,notnull
{return_url "/intranet-timesheet/absences/"}
}
The page contract effectively seals the trusted code in the HTML page from the "hostile Internet environment". In ]po[, a page contract is required and present for all pages.
SQL Injection attacks and "Colon Variables"
select * from users where user_id = $user_id;
The statement above looks like innocent piece of SQL retreiving information about a specific user, isn't it?
However, setting the value of $user_id to "0; delete from users cascade", the statement becomes a security holes that allows attackers to delete the database or to extract data.
This "SQL injection" patter is one of the most frequent sources of security holes in Internet applications. are variables values that are included in SQL statements. Such variables can be altered by a malicious user to contain additional SQL statements in order to extract information from the DB or to cause damage.
Now, please watch the SQL statement below:
select * from users where user_id = :user_id;
The ":" SQL variable behaves in a very different way then a "$" variable. Basically, the value of the colon variable is not "expanded" as part of the string. Instead, is is passed on to the database driver as a hole. As a result, the database would respond with an "invalid integer" error message or similar.
It is best practice in ]project-open[ to use colon variables. The compliance of the code with this standard can be checked semiautomatically using a Perl script.
Vulnerabilities
Vulnerabilities are flaws in computer software that create weaknesses in the overall security of the system. They are often detected either by the developers themselves, community members, security tool provider or customers.
Discovered vulnerabilities get the highest attention of the ]po[ Core team and are usually taken care of and fixed immediately. Before releasing the information on the SOURCEFORGE forum (https://sourceforge.net/p/project-open/discussion/295937) to the wider community, SaaS servers are patched clients with maintenance contracts are informed and provided with information on how to to address the issue.
Contact Us
Project Open Business Solutions S.L.
Calle Aprestadora 19, 12o-2a
08902 Hospitalet de Llobregat (Barcelona)
Spain
Tel Europe: +34 609 953 751
Tel US: +1 415 200 2465
Mail: info@project-open.com